Secure Socket Layer(SSL)
SSL stands for Secure Socket Layer. SSL was designed to permit web browsers and web servers to exchange sensitive information and prevent programs that could view the network traffic from reading the sensitive data.
The SSL protocol was developed by Netscape Communications in the 1990s. The company wanted to encrypt data in transit between its flagship Netscape Navigator browser and Web servers on the Internet to ensure that sensitive data, such as credit card numbers, were protected
The SSL goals are:
1. Confidentiality. The communication should be safe from eavesdropping.
2. Authentication of the Server. The client should be certain about the identity of the server.
3. Ubiquity, ease of use. There should be no barriers to adoption, neither on the part of the user nor the developer. The user should not have to take any particular action compared to non-SSL connections. SSL should fit easily into applications designed independently of SSL.
How SSL Works?
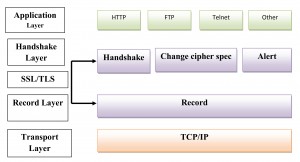
SSL uses a combination of public-key and symmetric-key encryption to secure a connection between two machines, typically a Web or mail server and a client machine, communicating over the Internet or an internal network.Using the OSI reference model as context, SSL runs above the TCP/IP protocol, which is responsible for the transport and routing of data over a network, and below higher-level protocols such as HTTP and IMAP, encrypting the data of network connections in the application layer of the Internet Protocol suite. The “sockets” part of the term refers to the sockets method of passing data back and forth between a client and a server program in a network, or between program layers in the same computer.
The four protocol layers of the SSL protocol (Record Layer, ChangeCipherSpec Protocol, Alert Protocol, and Handshake Protocol) encapsulate all communication between the client machine and the server.
1. Record Layer
This protocol provides two services for SSL connections:
- Confidentiality – using conventional encryption.
- Message Integrity – using a Message Authentication Code (MAC).
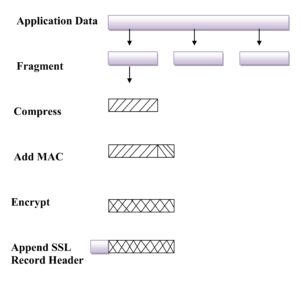
In order to operate on data the protocol performs the following actions:
1. It takes an application message to be transmitted and fragments it into manageable blocks. These blocks are 2 14 = 16, 384 bytes or less.
2. These blocks are then optionally compressed which must be lossless and may not increase the content length by more than 1024 bytes.
3. A message authentication code is then computed over the compressed data using a shared secret key. This is then appended to the compressed (or plaintext) block.
4. The compressed message plus MAC are then encrypted using symmetric encryption. Encryption may not increase the content length by more than 1024 bytes, so that the total length may not exceed 2 14 + 2048. A number of different encryption algorithms are permitted.
6. The final step is to prepend a header, consisting of the following fields:
- Content type (8 bits) – The higher layer protocol used to process the enclosed fragment.
- Major Version (8 bits) – Indicates major version of SSL in use. For SSLv3, the value is 3.
- Minor Version (8 bits) – Indicates minor version in use. For SSLv3, the value is 0.
- Compressed Length (16 bits) – The length in bytes of the compressed (or plaintext) fragment.
2. ChangeCipherSpec Layer
The ChangeCipherSpec layer is composed of one message that signals the beginning of secure communications between the client and server. Though the ChangeCipherSpec Protocol uses the Record Layer format, the actual ChangeCipherSpec message is only one byte long, and signals the change in communications protocol by having a value of ‘1’.